 Another global malware attack in June has left hundreds of IT staff scrambling to double-check systems or remediate infections. CTOs and CIOs are trying to explain, “Why were we hit? Why weren't better protections in place? Why didn't we know we were vulnerable?”
Another global malware attack in June has left hundreds of IT staff scrambling to double-check systems or remediate infections. CTOs and CIOs are trying to explain, “Why were we hit? Why weren't better protections in place? Why didn't we know we were vulnerable?”
Most of the scenarios occur because those involved do not have daily conversations with their IT infrastructure. Wait, what? You’re probably thinking, "You can't talk to your IT infrastructure. Are you nuts, Jordan!" However, the truth is you can, and you should be conversing with your infrastructure regularly. There
Fortunately, if you are leveraging Microsoft Azure and Power BI (Microsoft's Business Intelligence platform), all of this becomes much easier. Let's walk through some of the options available to an Azure consumer:
Azure Security Center Insights
Azure Security Center (ASC) is a tool provided by Microsoft to Azure consumers that
As you likely know, many of these items are key in maintaining regulatory compliance and posturing your security landscape. There are various tiers of this service, the highest of which will provide malicious activity and attack detection for your Azure resources. Once ASC is configured in both Azure and PowerBI, we can then take advantage of visual interaction with our security footprint.
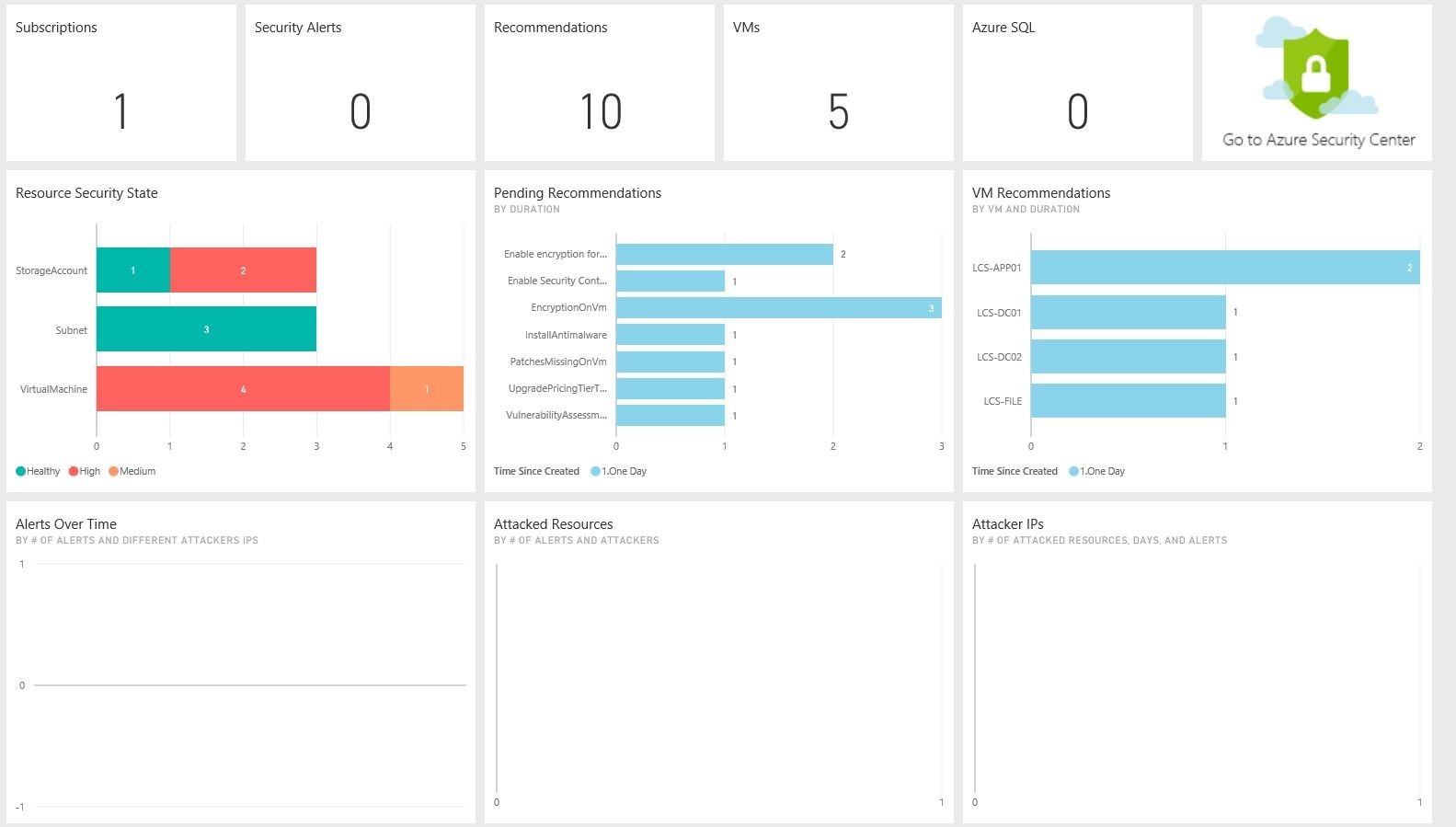
We can even drill down into each chart, to gain access to more specific data.
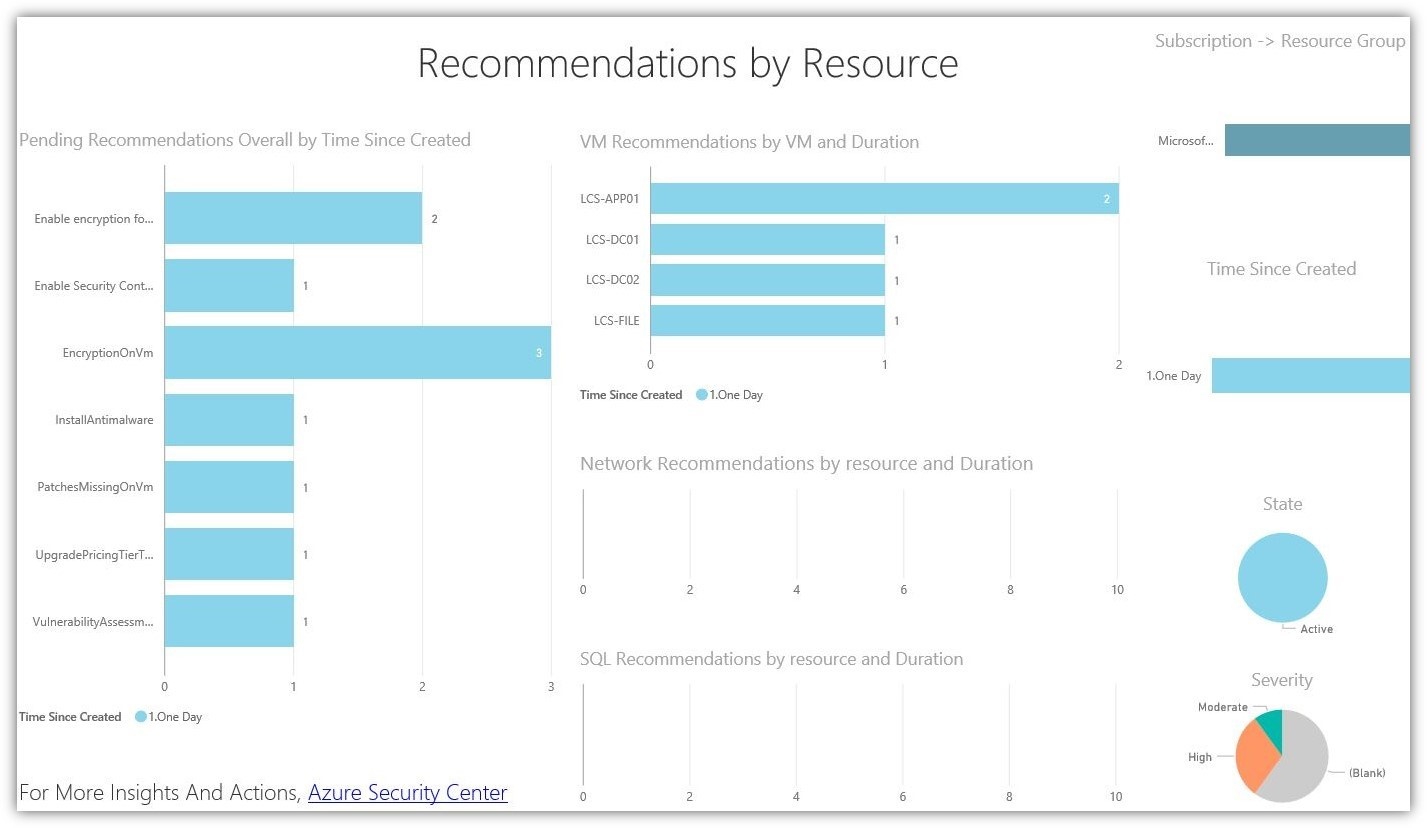
Using this data, we are able to keep an eye on our infrastructure to ensure certain security controls are in place, and that no strange activity is occurring within our virtual machines and network.
Azure Backup Reports
Now that we have data on our security posture, what happens when an attack is successful and we are now in BC/DR mode? The single most effective protection against ransomware is a good, healthy backup strategy. However, what I often find is that many believe their environments are being consistently and cleanly backed up, only to find that isn't the case when they go to restore. With Azure Backup Reports, you can now check on your data protection strategy at any time. Better yet, you can prove it with easy to read charts and graphs.
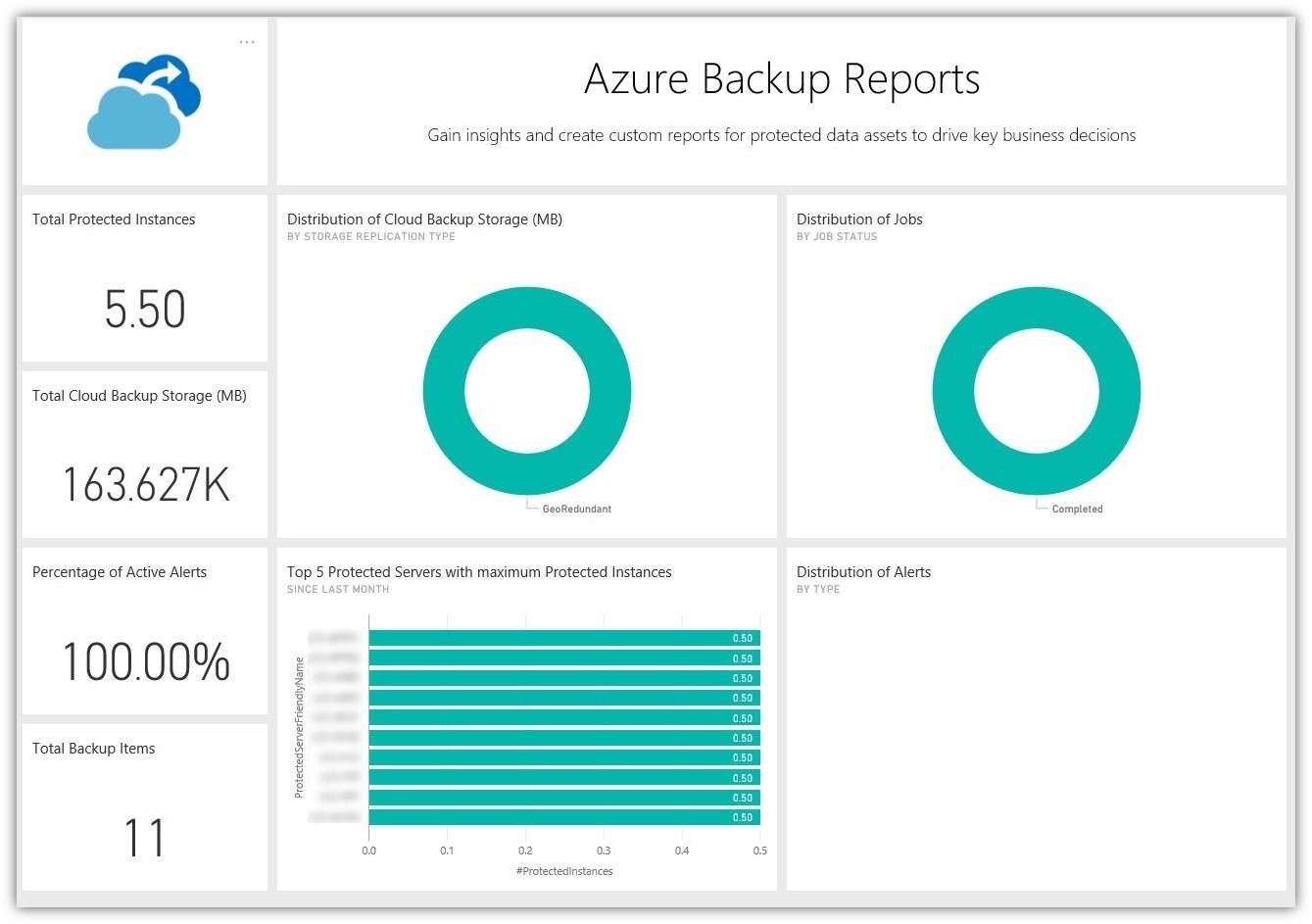
Perhaps most importantly, we can check on the health of our backup jobs to ensure there are no failed jobs or other issues.
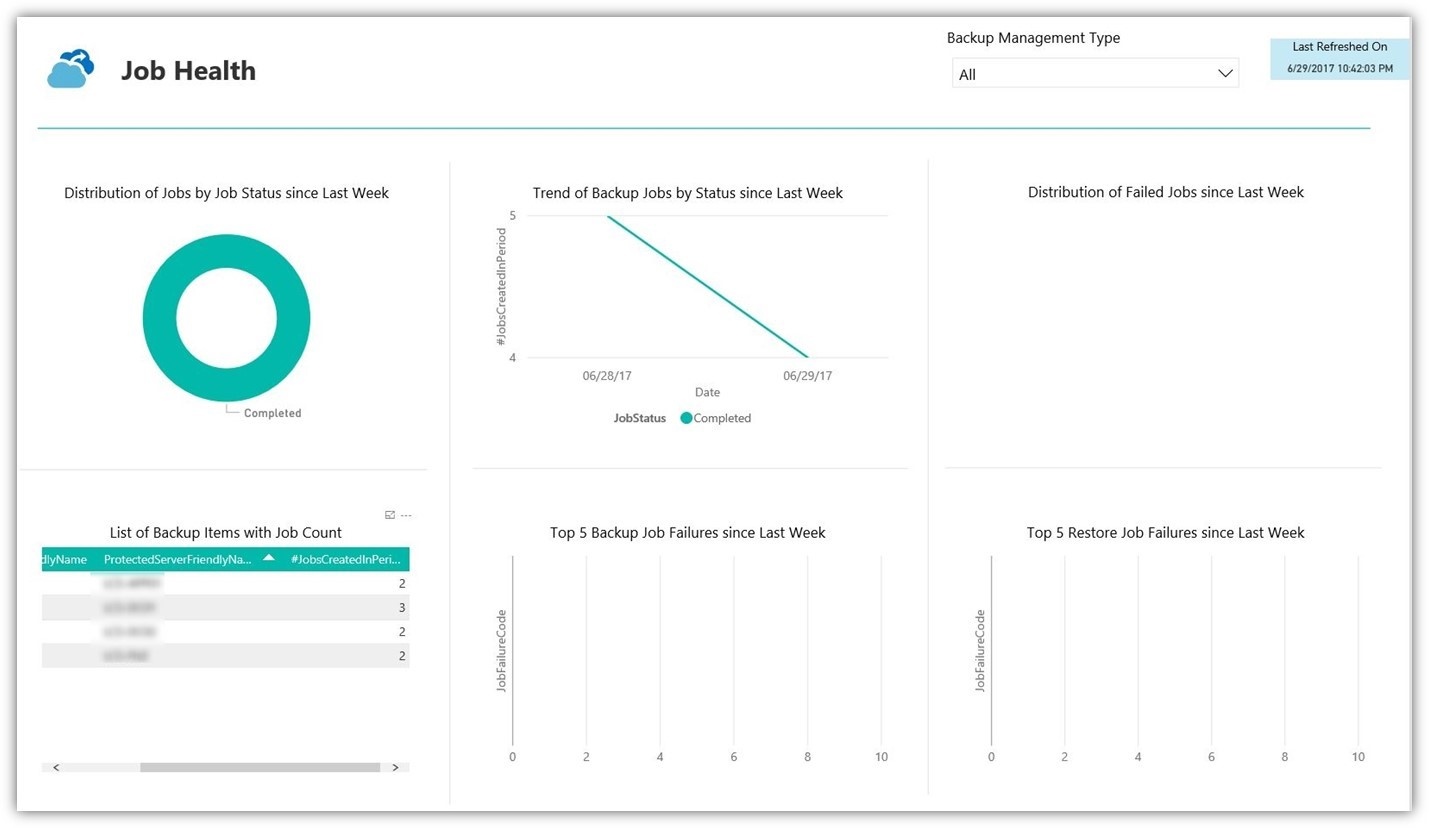
Remember when I said we should be talking

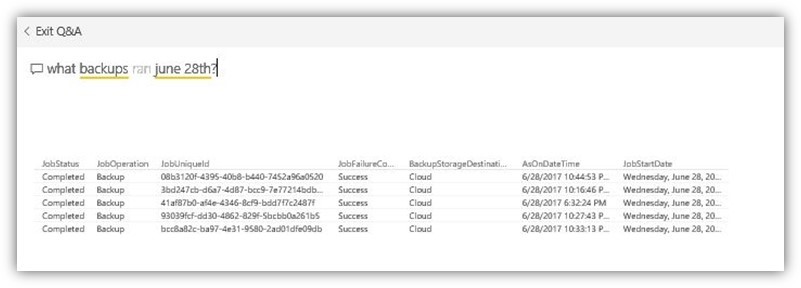
Told you I wasn't nuts!
Azure Audit Logs
We have gained insight into our security posture as well as our data protection strategy, but we can't stop there. Would those backups or security tools do you any good if they were deleted or deactivated? Of course not! We also need to ensure we have visibility and control over the management layer that controls these tool sets. That layer, of course, being our Azure subscription. With Azure Audit Logs presented in Power BI, we can dig into what's happening inside of our Azure subscription. We can see when resources are modified, deleted, deployed or otherwise acted upon. More importantly, we can see who is acting upon those resources. This is key from not only a security
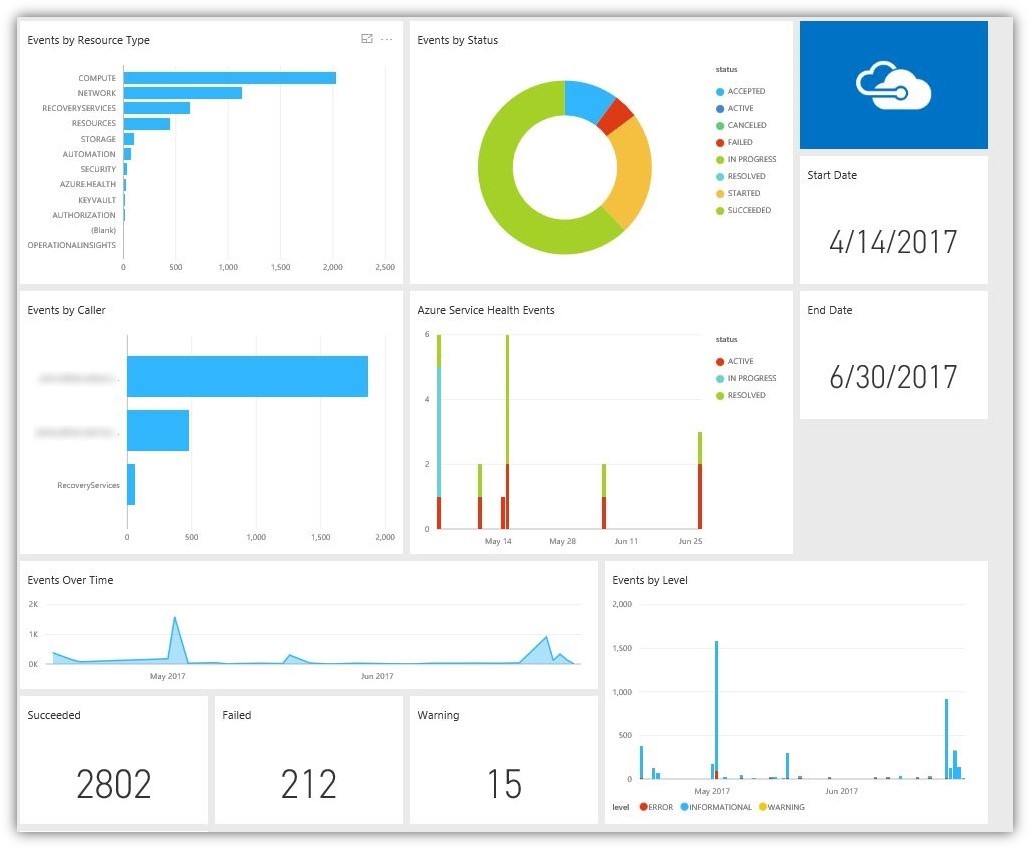
Another extremely important set of data in this dashboard is the Azure Service Health report. This provides insight into service degradation or outages that have occurred in regions where you have resources deployed. The data can be used to understand any strange behavior experienced by your Azure resources.
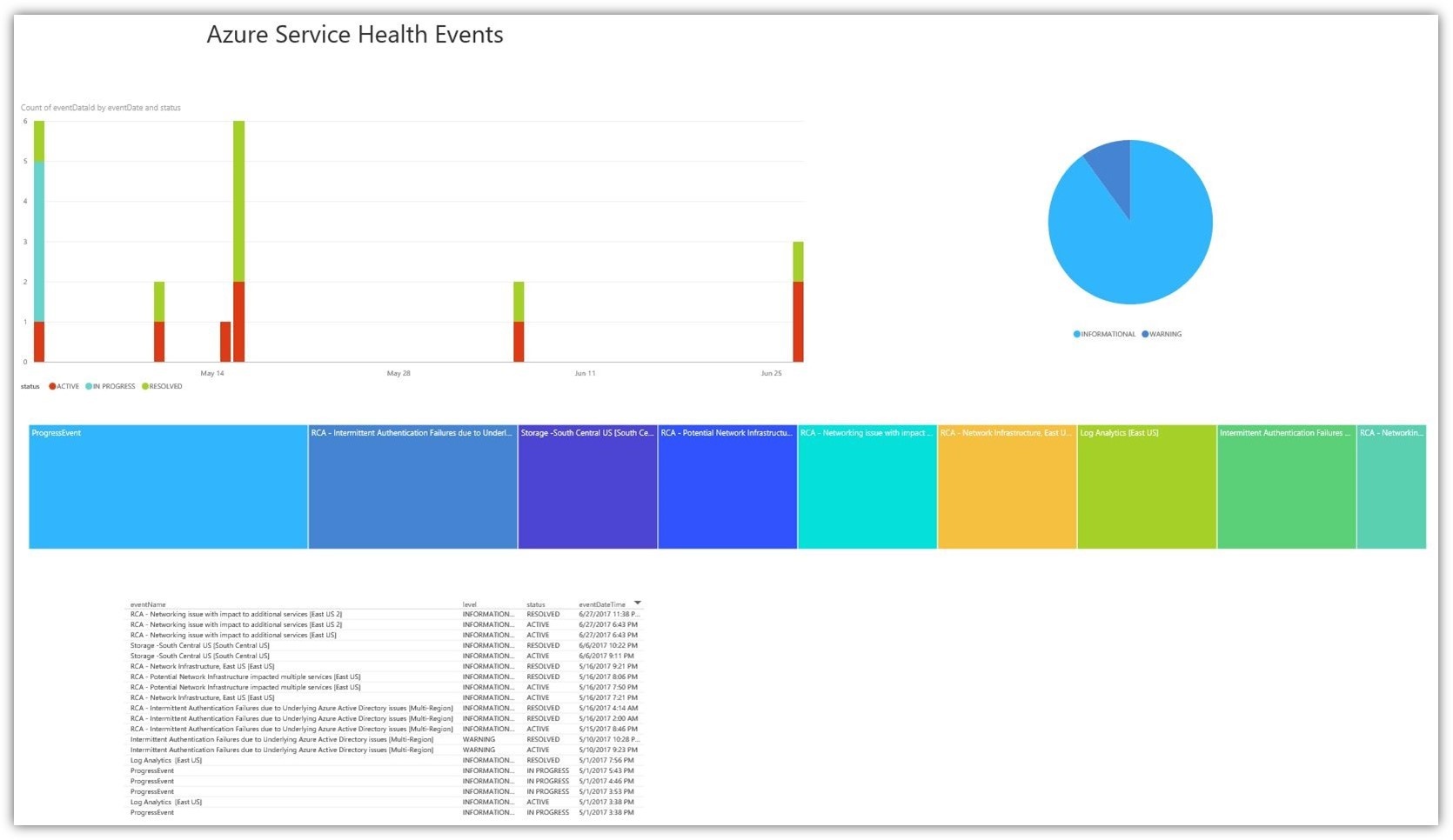
Improve Your Listening Skills
As you can see, your IT infrastructure is trying to tell you a lot. Why not listen to it? If you don't currently have these capabilities within your existing infrastructure, let this serve as an example of the benefits of undergoing a digital transformation within your organization and embracing the cloud once and for all.
 Contact TekLinks' Azure Solutions Engineer Jordan Helton.
Contact TekLinks' Azure Solutions Engineer Jordan Helton.

















