 During our internal penetration test engagements, we regularly come into contact with multifunction printers that are still using the default administrative login credentials. Obviously, using default credentials is never a good idea and I'd like to show how we can often pivot from these seemingly innocent multifunction devices and ultimately obtain total compromise of an environment.
During our internal penetration test engagements, we regularly come into contact with multifunction printers that are still using the default administrative login credentials. Obviously, using default credentials is never a good idea and I'd like to show how we can often pivot from these seemingly innocent multifunction devices and ultimately obtain total compromise of an environment.
In addition to default credentials issue mentioned above, one of the most common mistakes that we observe is MFP devices that have been configured to use privileged accounts (like Domain Admin) for sending scanned documents to network locations. For example, see below:
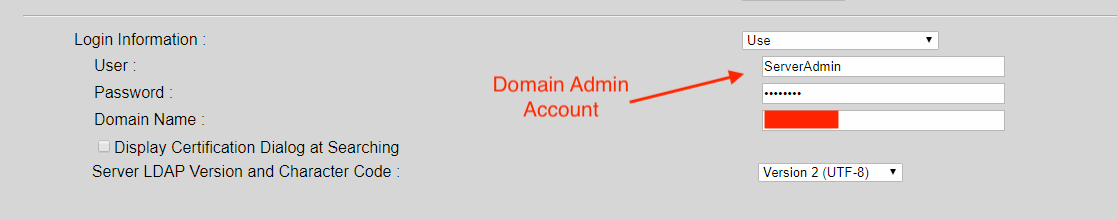
In many cases, it's fairly trivial for an intruder to access the masked password. All it requires (usually) is a small modification to the HTML code within a web browser.
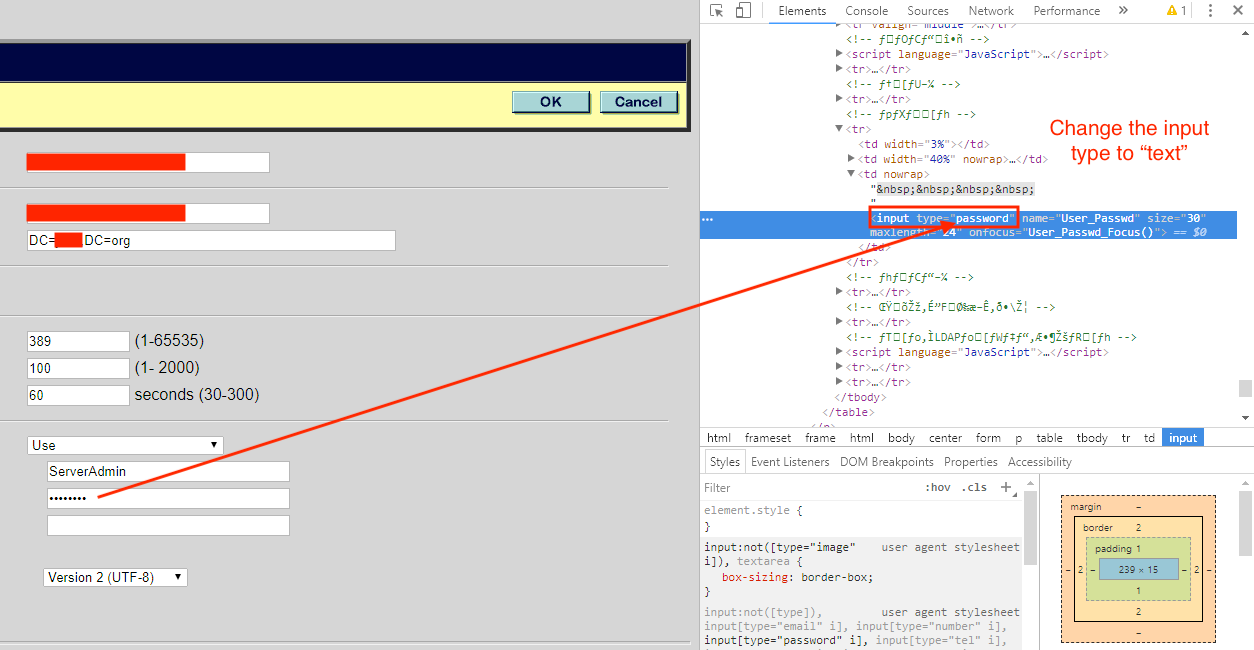
In this situation, we just needed to locate the correct form and change: input type="password" to input type="text"
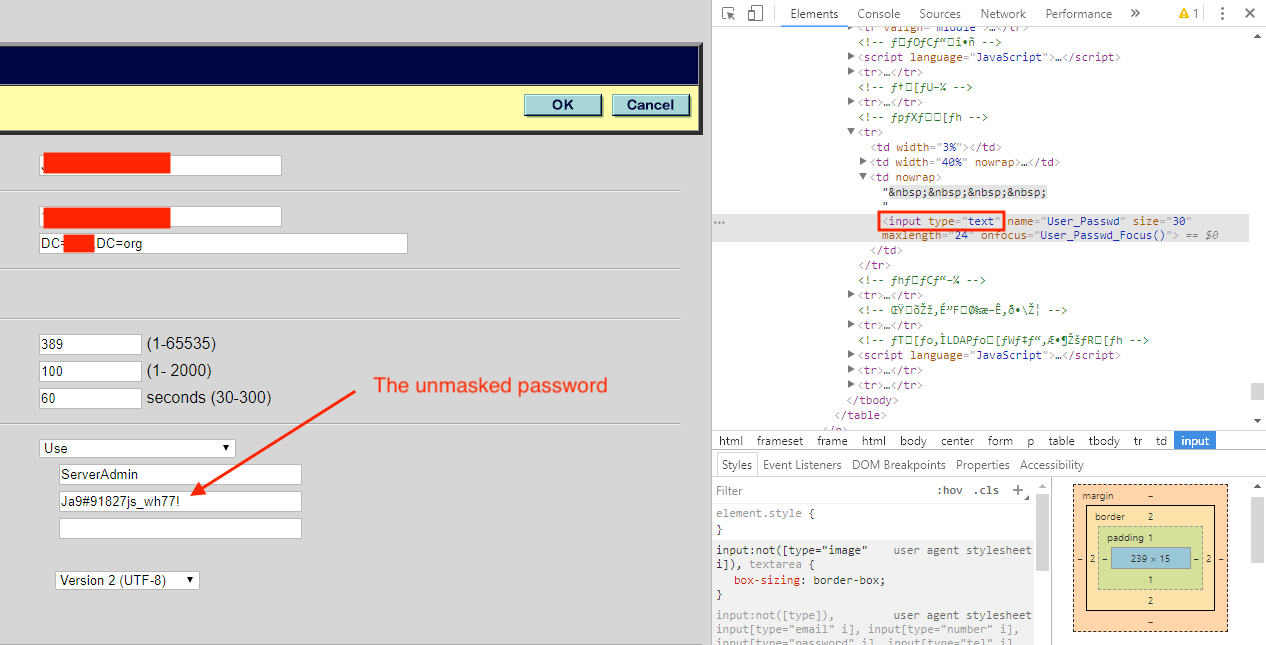
Secondly, this particular device was also configured to use LDAP. So, as the device is used throughout the day, authentication requests are made to Windows Active Directory servers. In my experience, organizations rarely utilize LDAP over SSL (LDAPS) in order to encrypt traffic and transmit information securely.
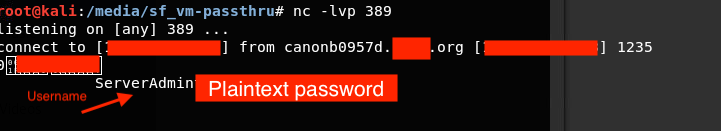
We can take advantage of this oversight by simply reconfiguring the MFP to use a different IP address for the LDAP server. Obviously, the IP address that we choose needs to be under our control and listening on port 389 (unsecured LDAP). When the MFP eventually makes an LDAP query, it should transmit the credentials back to us in plaintext.
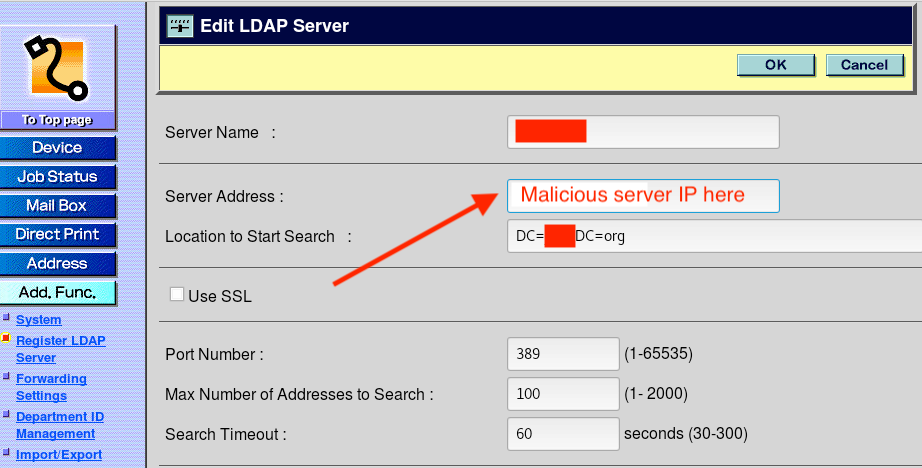
We can see (below) that we were able to catch the plaintext credentials of the account (Domain Admin) when an authentication attempt was made:
In closing, below are some suggestions mitigating MFP risks:
- Regardless of the type of device, always change the default password to something complex.
- Whatever you change the password to, don't reuse that password anywhere else.
- Understand the security capabilities that systems offer and utilize them to their fullest potential. For example, if your device supports LDAP over SSL ... use it.
- Organizations have gotten better about hardening servers and workstations - but don't neglect hardening other devices on your network too (printers, scanners, routers, switches, firewalls, etc). These devices often pose significant risk because they have unnecessary features enabled.
- Be extremely careful where you're utilizing your privileged accounts. Domain Admin-level accounts should never be used on MFPs, workstations, or other lower privileged systems that have a higher likelihood of being compromised.
In addition, we have not discussed conducting SMB relay attacks from MFP devices, but this is also a possibility and something that we'll cover in a future post.

Nick VanGilder is Lead Penetration Tester for C Spire Business' Cybersecurity Consulting Group. Contact him at ask@cspire.com

















