 Corporate Identities - that is, usernames and passwords - continue to be one of the main points of attack against businesses. For a reason! Many points of authentication are internet-facing humans who generally do a poor job of choosing passwords and can be easily manipulated into giving out their credentials.
Corporate Identities - that is, usernames and passwords - continue to be one of the main points of attack against businesses. For a reason! Many points of authentication are internet-facing humans who generally do a poor job of choosing passwords and can be easily manipulated into giving out their credentials.
Recently, my colleague Nick VanGilder took us on a journey of how hackers crack your corporate passwords. The end of the article provided a handful of tips for protecting passwords. Today, I want to show you how to make these tips actionable using Microsoft Azure Active Directory (AD).
What is Azure Active Directory?
Azure AD is an identity management and access service in Microsoft Azure. Azure Active Directory allows us to provide modern, secure authentication to a myriad of applications both on-premises and in the cloud. You can use Azure AD on its own or in conjunction with a traditional Windows Server Active Directory Domain. Azure AD is the authentication backbone for both Azure and Office 365, so if you are using Office 365 you are already using Azure AD.
For this blog post, we will be assuming you are using a traditional Windows Server Active Directory that has been extended to Azure Active Directory using the Azure AD Connect tool. In this scenario, your traditional Active Directory is the authoritative directory and Azure Active Directory will utilize identities already established in the traditional AD, including passwords. This creates a powerful, dynamic hybrid identity management system we can now use to protect our users anywhere in the world.
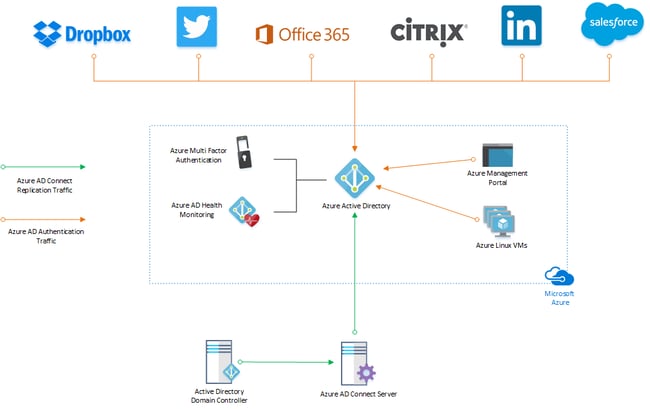
Hybrid Identity Topology utilizing Azure AD and Windows Active Directory
Complex Password Policy
Several of the tips mentioned in the aforementioned article deal with password complexity:
- Stop requiring employees to change passwords frequently
- Abandon traditional passwords in exchange for random phrases
- Perform regular audits to validate compliance with password policies
Much of this can be accomplished simply by utilizing the password policy group policy settings in your traditional Active Directory. These policies will replicate to Azure AD and thus be enforced across your entire hybrid identity control plane. While the use of phrases can’t be enforced, you can enable a high minimum number of characters in the password requirements. Maximum password age can be set to a high threshold to prevent users from being prompted to change passwords often. Train your users to utilize phrases rather than words, and routinely audit your password policies to ensure they have not been altered.
No More Weak Passwords
The attack method outlined in Nick’s article largely relied on users choosing passwords sourced from common words associated with the company itself or their environment. For example, a healthcare employee may choose a password that is based around the words “nurse” or “doctor”. Users may also select passwords based on their surroundings and environment, such as seasons, local sports teams, landmarks, etc.
Good user-awareness training will steer employees away from these types of passwords, but otherwise little could be done to prevent the use of common words. Fortunately, that is no longer the case. Recently released in public preview is the custom banned passwords feature for Azure AD. This allows us to supply words common to our company or environment that we suspect users will choose. This feature also allows you to effectively ban a previously used password that was compromised, or you simply want to ensure is never used again.
As a part of this new feature, Azure AD automatically checks variations of the words in the list to ensure users aren’t circumventing the policy. For example, entering “healthcare” into the list will block passwords such as “hea1thcar3” or “healthcare001”.
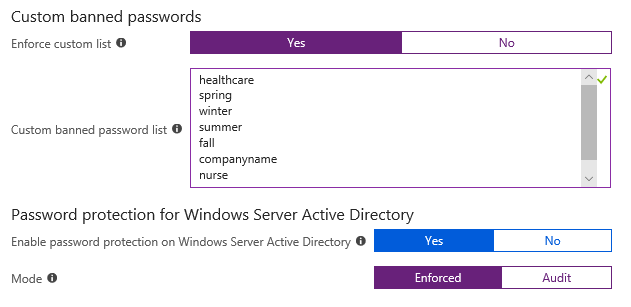
Azure AD Custom Banned Passwords Configuration Screen
Conditional Access
We are in the age of the cloud. Applications are moving online and becoming globally accessible at an incredible rate. The very idea behind cloud software suites like Office 365 is to create mobile workforces that can collaborate across large distances at any given time. As a result, our users may begin to access these services from multiple devices and locations that we do not trust.
Azure Active Directory helps us define rules and restrictions on how and where our applications are accessed using a feature called Conditional Access. Policies defined within Conditional Access define a user, group or all users and place restrictions on accessing one, some, or all Azure AD cloud applications via several control variables. For instance, we can specify that users accessing Office 365 must use Azure Multi-Factor Authentication to do so. That may be too restrictive for day-to-day activities on networks we trust (i.e. our office), so we could then alter the same rule to only enforce Azure MFA if a user is accessing Office 365 from any network other than the office. Other controls are also available, such as restricting the access to cloud applications to computers that are known to Azure AD and Active Directory. This ensures users access corporate applications from devices that are trusted, no matter where they are.
Additionally, conditional access policies can be used to ensure your administrator accounts adhere to strict standards automatically. Conditional Access policies are an extremely powerful way to secure corporate assets that are internet accessible with additional protections, while ensuring the global mobility the cloud age requires.
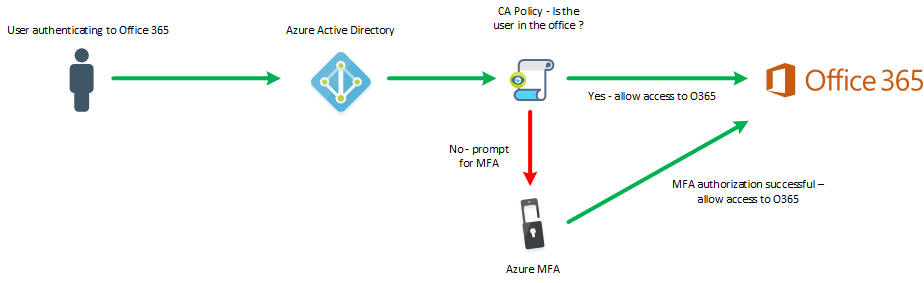
Azure AD Conditional Access Scenario Workflow
Avoiding Reusing Passwords
Shared user accounts and/or sharing passwords should be avoided. However, despite knowing it is a poor security choice, the practice continues at an alarming rate. Azure AD can help in this area by acting as a password repository in a couple of different ways. First, users can store credentials for 3rd party cloud applications within Azure AD and use Azure AD to launch those applications, without the need to interact with that particular applications password each time. Additionally, IT Administrators can input accounts into a user’s Azure AD application portal and allow the user to access an application without ever seeing or interacting with the actual password for that 3rd party application. Ideally, we would reroute authentication for 3rd party apps to use Azure AD natively, but in instances where that isn’t possible this solution is a good stop gap.
One area where password/authentication sharing is commonly accepted is Linux servers. Typically, an SSH certificate is generated for a server and passed around to various staff members who need access. While there are a lot of merits to certificate-based authentication, issues arise when dealing with employees who have left or certificates that have been lost or misplaced. If you are running Linux servers in Azure you can utilize a new (preview) feature that allows you to authenticate to those servers using Azure Active Directory. This brings Linux and Windows authentication under a single umbrella and allows for easy delegation of permissions for cross-platform server management.
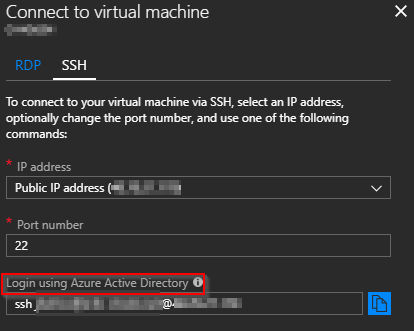
Azure AD login context on a Linux VM in the Azure Portal
Enable Multi-Factor Authentication
Multi-Factor Authentication (MFA) is not a new technology but industry advice to adopt it has become increasingly louder in recent years. This is because MFA is likely to be the strongest layer of protection in your journey to protect your user’s identities. You may have heard that MFA is frustrating to use, but improvements to authentication approval methods and the benefits gained from using the technology far outweigh any inconvenience.
Azure Active Directory has its own Multi-Factor Authentication add-on called Azure MFA, which can be layered onto any application that authenticates via Azure AD, including Linux virtual machines in Azure, Remote Desktop Gateway, Citrix and thousands more. If you still have legacy applications that authenticate through traditional Active Directory, you can tie in certain 3rd party MFA providers (such as DUO) to cover both Azure AD and traditional AD authentication with a single source of MFA.
Azure MFA approval prompt
Password Protection: How the Pros Do It!
Attacks on corporate identities will continue to escalate in the cloud era. Thankfully there are also cloud era tools, such as Azure Active Directory, that allow IT Administrators to level the playing field against bad actors. Modernize your identity strategy today and sleep better tonight. If you need assistance in this area, we would love to help! C Spire Business offers a variety of services around both identifying security risks and providing solutions to solve for those risks.

















