Security is a topic that is bound to either raise your blood pressure or put you to sleep.
Unfortunately, most written materials around technology security are either deliberate scare tactics or too technical, ambitious, or priceyto be immediately helpful. As a leader in your business, it's your responsibility to get your head around the whole security thing. But for most, it’s impossible to shore up every conceivable security vulnerability at once. Doing so is not only financially impractical, it’s simply not the best way to become secure.
Data Security: Protecting data, such as a database, from destructive forces and from the unwanted actions of unauthorized users
The reason is because security is not just a list of checked boxes. It is a cultural mindset toward technology and data that exists throughout your organization because that is what is best for your employees, your company, and your customers. A culture of Security begins at the top.
Today begins an 9-week journey in which we will peel back the 7 Layers of Data Security. By reading this series, you are taking long strides toward building a culture of security that will endure for years, weather future challenges, and meet every compliance and regulatory requirement you face.
The Path to Security
The path to security is a series of baby steps.
Just like our physical health, it's common to aggressively pursue our goals in fits and starts, only to shortly get overwhelmed and burn out. In business, as in fitness, it's better to implement a series of simple, gradual changes over time to develop a healthy lifestyle of security.
Toward that end, business leaders need practical, concise, relevant guidance on this issue. So C Spire has created a primer on business security. This primer is designed to provide you three tangible benefits:
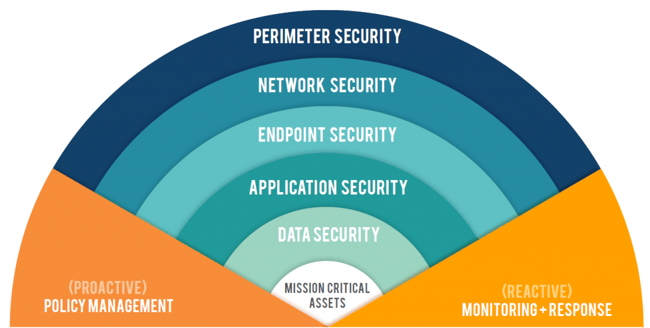
- A visual representation of the 7 layers of security necessary to protect your company data
- An executive summary of these 7 layers
- A brief explanation of the technologies available to help secure your company data within each of these 7 layers
7 Layers of Data Security
Every company network is different. As such, there is no simple, one-size-fits-all, three-step plan for putting a pad-lock on your company's technology. So instead of describing every possible contingency and how you should address it, let's imagine your network as a series of layers that each perform a different function in protecting your Mission-Critical Assets.
These assets are the reason we have security. They are the meat and potatoes of your business. If they are compromised, it would have a direct impact on your ability to operate. Because they are so vital to our businesses, we wrap them in layers of security so that even if one of those layers is breached, our work can continue.
The graphic below illustrates these layers and how they function to protect your Mission Critical Assets. This blog series will address each of these layers and identify some of the resources available to understand and improve your current situation.
Up Next: Mission Critical Assets
For the next eight weeks, we'll be diving into more depth on each level of this diagram in this series. On June 14, we discuss your company's Mission-Critical Assets and why they form the axis around which all your security actions should revolve.