Note: Today is week 7 of a 9-week blog series in which we are peeling back the 7 Layers of Data Security. Catch up on the series here.
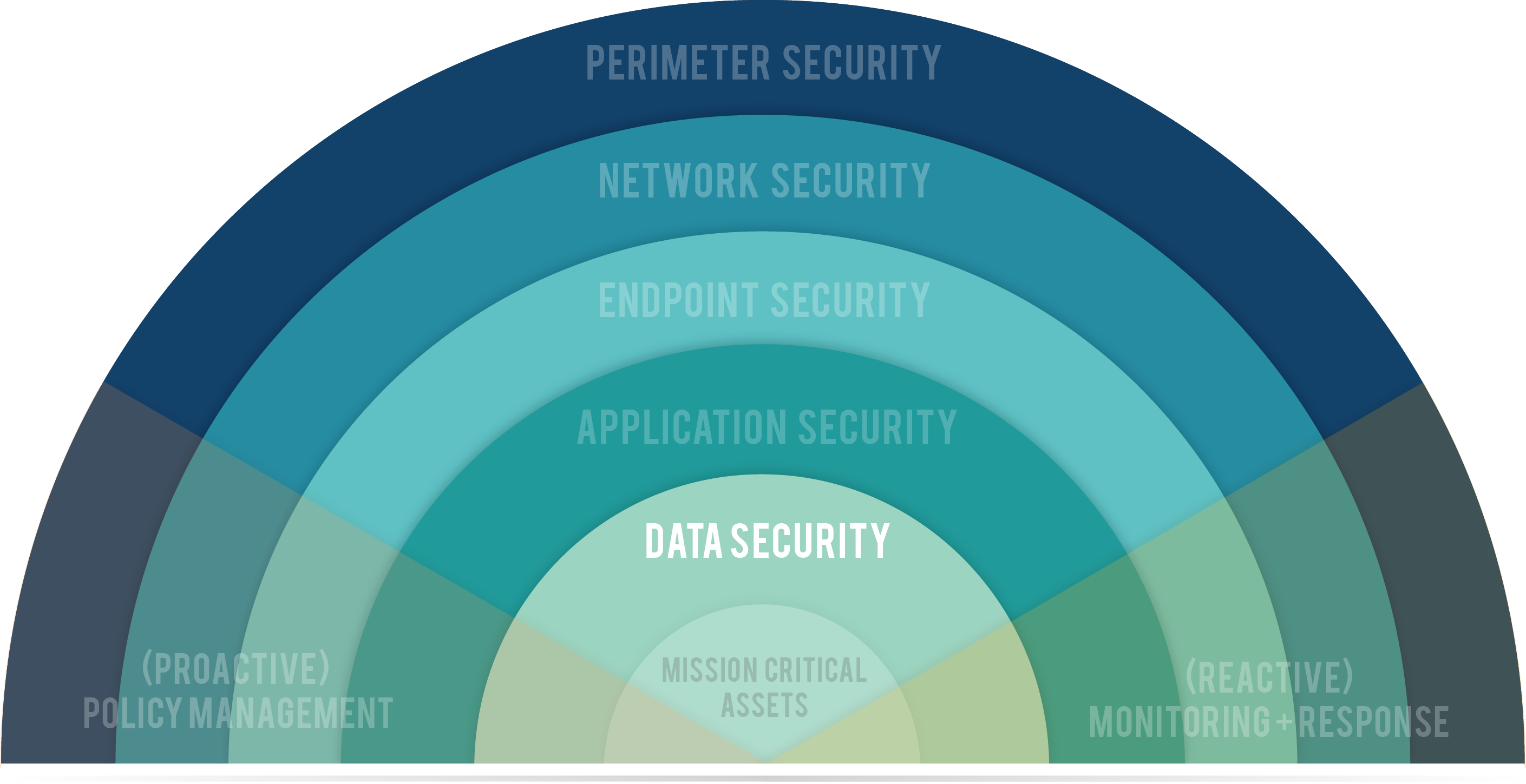
Data Security is protecting your organization's critical files against corruption, manipulation, theft, erasure.
Because your data is so important, you hide it in the center of your castle — surrounded by moats, archers on turrets, drawbridges. If an intruder gets through those defenses, they have to pass through dark labyrinths, trip wires, hidden pits of snakes, and pressure-activated plates that launch poison-tipped darts. If, by some miracle, every layer of security you've put in place fails, your final option is to booby-trap the treasure itself. This is data security.
 Data is the Commodity of Cybercrime
Data is the Commodity of Cybercrime
The term "data security" is often used synonymously with "security," "business security," and "network security" because the primary objective of cybercrime is data.
Credit card numbers, bank account numbers, social security numbers, health records, personal information, intellectual property, are all data. Even if someone were to get access to your database, there are things you can do to protect the data itself.
In the U.S., about 12,000 laptops are lost or stolen every week.
Keys to Data Security
Data security is the process of making data as difficult as possible to view, read, manipulate, and remove. As such, the primary tools used to secure your data are usually lumped into three categories:
- File Encryption & Disk Encryption
- Encryption is the act of scrambling data so that it is only readable to people with the Key. With File Encryption the individual files on a hard drive or other device can be directly encrypted. By encrypting the data itself, it will remain secure regardless of where the file is stored. You could email an encrypted file safely. With Disk Encryption, however, only the device that holds the data is encrypted. Think of Disk Encryption like a safe. Only the people with the right code can access the safe. But once the contents are removed from the safe, they are no longer secure.
- Backups
- In addition to outright theft, data must be protected from corruption. Data corruption can be malicious and deliberate or benign and purely a malfunction of technology. A backup strategy is an essential step in protecting against data corruption from either source. It is important to add here that not all backups are created equal. Are your backups performed regularly. Ensure that your backups are being tested. Occasionally, perform a test to ensure your policies and processes will function as planned in an emergency.
- Data Erasure
- When retiring a piece of equipment — laptop, server, USB drive, external hard drive, printer/copier, etc—are you sure all the data has been completely removed? Anything with a storage element can retain data and therefore presents a security risk. When disposing of old equipment, whether you're giving it to someone else or sending to the electronics recycler, make sure your data is properly wiped.
According to the Ponemon Institute, a laptop is stolen every 53 seconds.
Tools to protect your data
- Data wiping and cleansing services
- Data Drive Encryption/Full Disk Encryption
- File encryption software
- Data backups (regular and tested)
- Two Factor Authentication
- Data Integrity Monitoring
- Enterprise Rights Management
- Identity and Access Management
- Data Loss Prevention
Security Assessment
Now is the time to consider the next step toward building a culture of security within your organization. Request a Security Assessment from TekLinks’ team of experts.
Catch up on the rest of the 7 Layers of Data Security series here.
Next week we will discuss Preventative Security.
WHO IS TEKLINKS? A national leader in cloud computing, managed services, engineering services, and value-added resale. We’re a team of expert techies and business professionals who are passionate about building valuable relationships and getting things done right. Simply put: We make IT work for business.