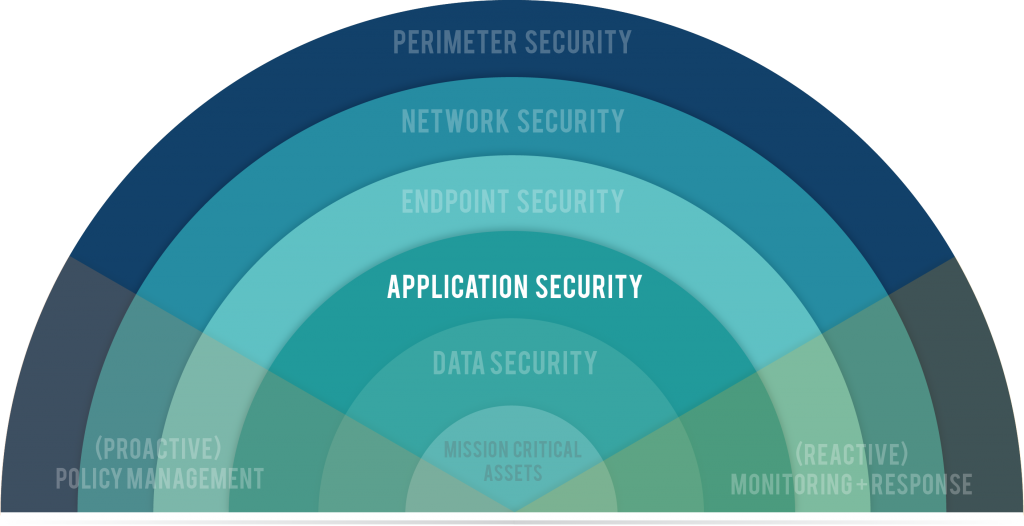
Note: Today is week 6 of a 9-week blog series in which we are peeling back the 7 Layers of Data Security. Catch up on the series here.
Application Security is the process of securing the software an organization uses to perform a particular function.
Microsoft Exchange, Quickbooks, Greenway, Great Plains, Dropbox, CAD, Minecraft. They’re all applications.
And while each application performs a unique function in your job and business, each application also presents a unique security vulnerability. The programs you use occupy a “seat,” on your network. Your network provides users access to the software, and the application likewise provides access to your network.
You’re Only As Secure As Your Weakest App
Applications are one of the primary ways cybercriminals do their dirty work. They infiltrate their victims’ databases at the weakest point, which is often third-party software. When a program is hosted on your network, it provides an “on-ramp” to your database.
Zero Day Threat – A zero day vulnerability refers to a hole in software that is unknown to the vendor. This security hole is then exploited by hackers before the vendor becomes aware.
You’re Only As Secure As Your Weakest App’s Weakest Point
Applications have weaknesses. When hackers discover a vulnerability in Microsoft’s OS that they can exploit to cause harm, it’s called a “Zero Day” threat. Microsoft has to scramble to provide a patch that addresses that vulnerability. Until they do, that app’s weakest point is your weakest point — unless you work proactively to safeguard against these types of threats.
How Application Security Works
Application security is all about isolation. Each application hosted on or accessed via your network needs controls around them so that if that application is exploited, the exploit won’t be released to the whole environment.
Depending on how your network is designed, application controls can perform the following functions:
- Prevent unauthorized applications from running
- Ensure authorized applications only perform the way they are supposed to
- Limit access to external web applications
Awareness
The other primary asset in any defense strategy is awareness. An ounce of prevention is worth a pound of cure. A stitch in time saves nine. The best defense is a strong offense. There is no substitute for paying attention to the security ecosystem and hearing about threats in order to address them quickly.
75% of attacks take place at the application layer.
Application Security Tools
The tools below can help partition off the applications in your network from the rest of your network.
- Software restriction policies and/or software inventory (only approved apps are allowed to run)
- Personal firewalls
- Controlling through OS
- Web browser sandboxing
- Database Monitoring
- Unified threat management through firewall
- Nextgen firewalls
- Cloud application service brokers
Security Assessment
Now is the time to consider the next step toward building a culture of security within your organization. Request a Security Assessment from TekLinks’ team of experts.
Catch up on the rest of the 7 Layers Data Security series here.
Next week we will discuss Data Security – protecting your organization’s critical files against corruption, manipulation, theft, and erasure.
Join our Twitter chat at 2pm CDT / 3pm EDT today, July 12, as we talk about security culture at the application level. We're using the hashtag #chatTekLinks
WHO IS TEKLINKS? A national leader in cloud computing, managed services, engineering services, and value-added resale. We’re a team of expert techies and business professionals who are passionate about building valuable relationships and getting things done right. Simply put: We make IT work for business.