Note: Today is week 2 of a 9-week blog series in which we are peeling back the 7 Layers of Data Security. By taking this journey, you are making long strides toward building a culture of security that will endure for years, weather future challenges, and meet every compliance and regulatory requirement you face. Read the first post.
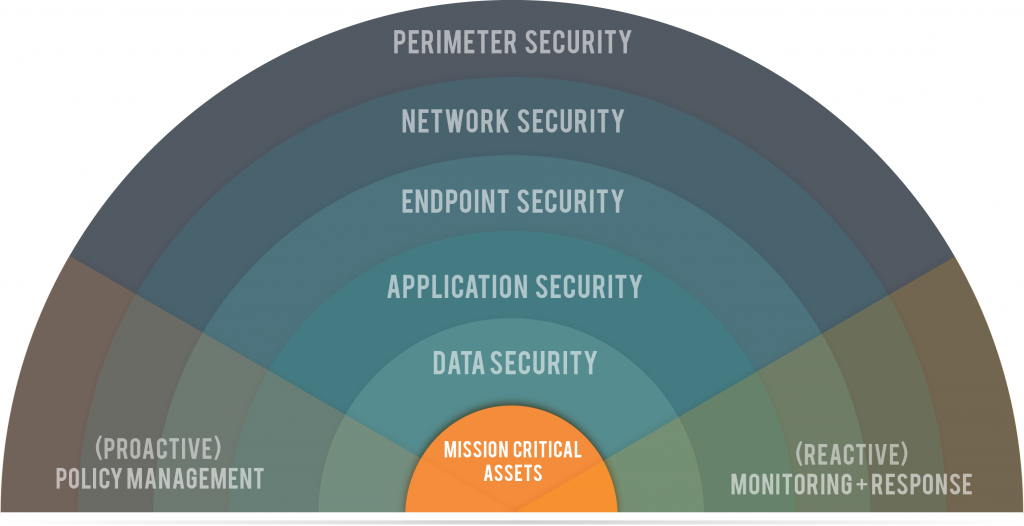
The term "Mission-Critical Assets" makes it sound like your business is of strategic significance in a military operation. In a very real sense, this analogy is appropriate. Malicious forces on multiple fronts are confronting your business every day. What they're after differs from attack to attack. As a business leader, however, your job is to protect your Mission-Critical Assets.
Examples of Mission-Critical Assets
Healthcare
- Electronic Medical Record (EMR) software
Engineering
- Auto CAD software
- Database of schematics
Manufacturing
- OS for manufacturing equipment
Financial Services
- Customer financial records
Cloud and IT Services Companies
- Central network and database environment
- Ticket management software for support requests
There is no one-size-fits-all approach to securing those assets because every business' network and important assets are different. However, knowing what technology is at the core of your business allows you to prioritize how you begin to secure that technology. So, all security conversations must begin there.
"If companies don't know what data they have and how to categorize it, they tend to value everything as imperative, just in case. When you're deciding how best to protect your data and applications, the key to success lies in identifying what's mission-critical — that is, what your business can't live without."
Make a List
To determine what are your company's Mission-Critical Assets, complete the following sentences in your own words:
- Without access to ____________________, my employees could not do their jobs.
- If ____________________ was not functioning, my business would not make money.
- If the database of my company's ____________________ was compromised, released to the public, stolen, it would be very, very bad.
Using this framework, make a list of an many Mission-Critical Assets as you can think of.
While you likely already had a good picture of what technology resources are most important to your organization, getting them in writing is a necessary first step in establishing a security strategy.
With these assets documented, we can begin to outline how to protect them.
Layer 1: Perimeter Security
The first line of defense around Mission-Critical Assets in any environment is called "Perimeter Security." We discuss how it is the demarcation between you and third parties here.
WHO IS TEKLINKS? A national leader in cloud computing, managed services, engineering services, and value-added resale. We’re a team of expert techies and business professionals who are passionate about building valuable relationships and getting things done right. Simply put: We make IT work for business.