Note: Today is week 4 of a 9-week blog series in which we are peeling back the 7 Layers of Data Security. Catch up on the series here.
Layer 2: Network Security
Network Security is protecting parts of your network from other parts of your network.
The words "Network" & "Security" are pretty common (or thrown around frequently in the tech world), so when used together, they can mean different things to different people. For the purpose of this discussion, we're using it to describe the process of partitioning your network so that two things happen:
- People can access the areas of the network appropriate to their job function
- Devices can only access areas of the network appropriate to their function
Basically, Network Security comes down to this: there is no reason that every department and job function should have access to every area of your network.
For Example ...
Tim, the office administrator, should only have access to what is relevant to his job. Cheryl, the IT Director, should have greater access to the network – but even for Cheryl, it may not be relevant to have access to everything. Unfortunately, it is entirely too common to see infrastructures where large groups of people are given complete network access. This exposes your network to threats. But to what threats exactly?
Why Do We Limit Access?
Two answers: rogue employees and rogue devices.
- Rogue Employees – We segment and limit access to protect the company against both intentional malice and unintentional mistakes. There is no 100% problem-proof network. But it’s your job to make it as difficult as possible for a large-scale breach to occur or mistake to happen. Each user must have only the access that aligns with their job function.
- Rogue Devices – It’s technology. It breaks. Software becomes outdated. Platforms don’t sync. We also segment and limit access to individual devices to protect the company as a whole in case a device is lost, stolen, or compromised.
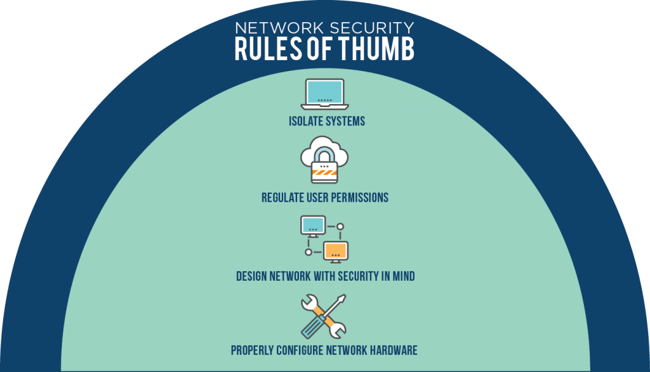
Network Security Rules of Thumb
- Isolate systems – There is no reason the CEO’s computer could ever route to the SAN
- Regulate user permissions – Tier access. Give every employee the strictest access permissions by default. Increase permissions as necessary.
- Design the network with security in mind, or redesign if necessary – Don’t assume your network is designed securely. Do your due diligence. Any time and effort spent shoring it up will pay long-term dividends.
- Properly configure network hardware – There is a right and a wrong way to configure equipment.
With the right guidance, your network should function like a watertight ship. A breach in one area shouldn’t sink the ship.
Consider these technologies to help secure your network:
- ID/IP with Cisco, Fortinet, AlertLogic
- Threat Management (Alertlogic)
- Network Configuration
- VoIP Encryption
- Web Content Filtering
- Message Security (SpamSoap)/Spam Filtering
- Network Access Control (Cisco CSE)
- SSLVPN (Remote VPN)
Security Assessment
Now is the time to consider the next step toward building a culture of security within your organization. Request a Security Assessment from TekLinks’ team of experts.
Catch up on the rest of the series here.
WHO IS TEKLINKS? A national leader in cloud computing, managed services, engineering services, and value-added resale. We’re a team of expert techies and business professionals who are passionate about building valuable relationships and getting things done right. Simply put: We make IT work for business.