Note: Today is week 8 of a 9-week blog series in which we are peeling back the 7 Layers of Data Security. Catch up on the series here.
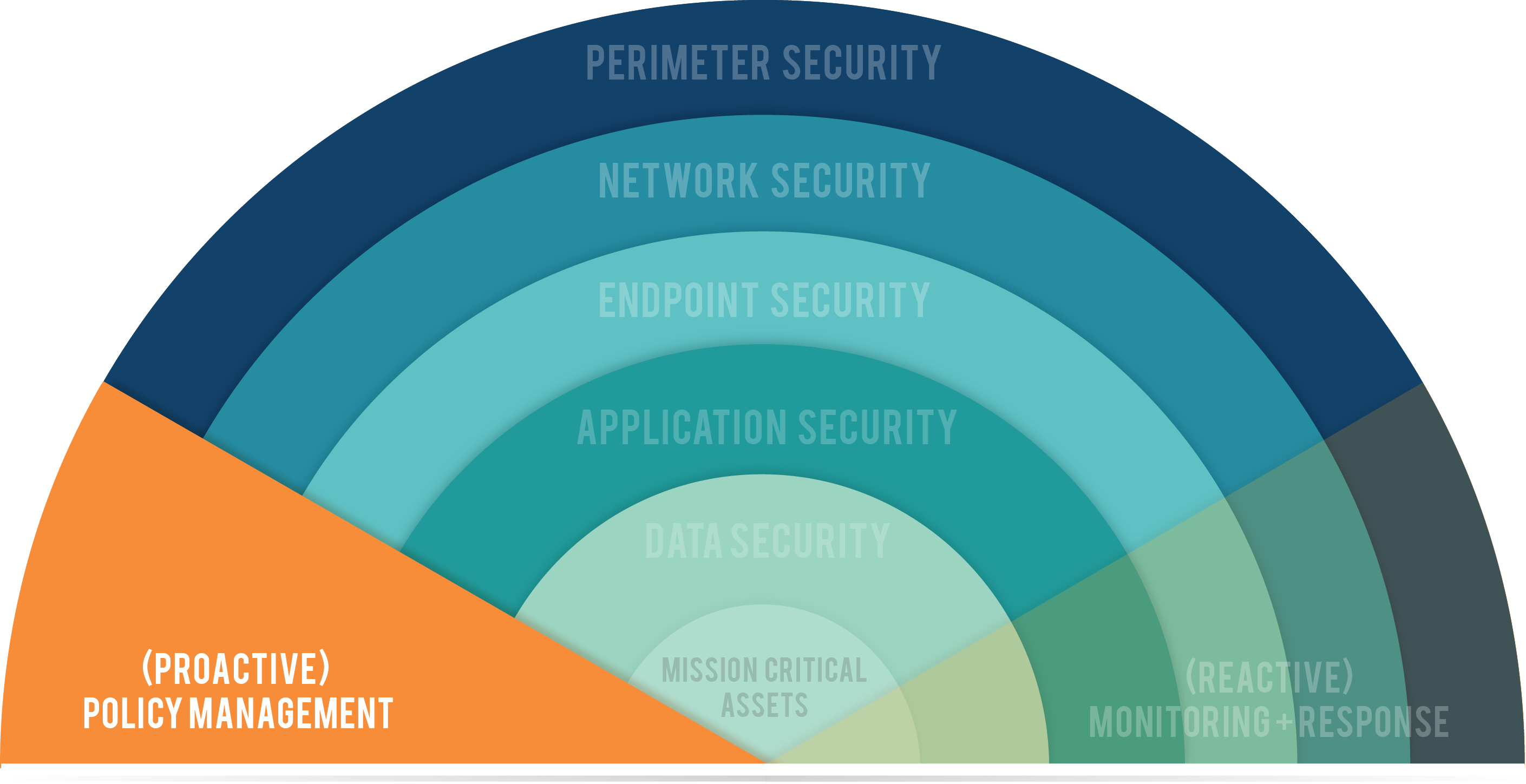
There are two components of technology security that span all the other layers: Policy Management (Preventative) and Security Operations (Monitoring & Response). There are proactive and reactive elements to every security strategy. Today we focus primarily on what an organization can do to prevent security breaches.
Preventative Security
Your preventative security strategy will address four tactics:
- Policy Management: Creating and maintaining living documents that outline exactly how employees and technology should function to protect your IT assets.
- Risk Assessment and Management: Evaluating the potential risks that threaten your organization’s IT assets.
- Testing: Ensuring your policies and technology function as they are intended.
- Training: Ongoing staff education about security and their role in protecting the organization.
Policy Management
Policy Management is the backbone of any technology security strategy. There are several reasons why:
- It is preventative and proactive
- It addresses the technical and personnel sides of security
- It documents your strategy, which is a huge help in remediating security breaches or in the event of an audit
- It reveals weaknesses, threats, and opportunities in your security strategy
- It provides the framework for implementing security tools properly and effectively
Without a policy management strategy, all other efforts will fall flat, unable to execute effectively across the organization. Obviously, policies aren't a silver bullet to organizational security. They cannot create themselves. They cannot enforce themselves. They cannot educate your employees on their own. Those tasks fall to you.
Acceptable Use Policy
Having the policy isn’t enough. You need to educate your employees on it. That’s where an Acceptable Use Policy comes in.
An Acceptable Use Policy is a description of how the company plans to educate its employees about protecting company assets. It also includes an explanation of how security measurements will be carried out and enforced, and a procedure for evaluating the effectiveness of the security policy to ensure that necessary corrections will be made.
Risk Assessment and Management
Knowledge is power. The more you know about the threats and risks your organization faces specifically, the better able you will be to prevent and respond to them. However, most business leaders prefer to take the Ostrich Approach to security, burying their heads in the sand and thinking "If I can't see it, it goes away."
While much easier, it is completely irresponsible (not to mention dangerous).
Every security strategy is different because each business is unique in the challenges it faces, the goals it pursues, the tools it uses, and its cultural climate. Like a suit of armor, no one suit will fit every soldier perfectly. They need a custom fit. A risk or vulnerability assessment takes a deep dive into your situation and clearly outlines your priorities. It's an essential step. It's also an ongoing mindset.
Get in the habit of asking "How does this new _________ affect my security situation?"
It could be a new piece of software, a new policy, a new customer, a new line of business, a new position in the company. Regardless, get used to thinking about it from the perspective of how it affects your overall security health.
Testing
The Law of Security Entropy
In nature, life, and IT security, everything wants to slowly drift toward disorder, disrepair, and chaos. In security, at least, testing is entropy’s antidote. Testing can be defined simply as finding the weak points before they find you.
Structural engineers test bridge designs before committing to one. Car manufacturers test a new model for safety before releasing it to the public. Companies should test their network security before relying on it. Network penetration testing (or "pen testing"), for example, mimics a hacker by attempting to break into your network. This process reveals weak points in your environment that need to be shored up. Other types of testing include threat modeling, which hypothesizes likely shapes the threats you face may take.
Training
Your employees are your weakest link. Plain and simple - a company's staff is its single largest security threat. [A recent independent study by IBM found that human error contributes to 95% of all cyber security incidents.]
In fact, the cause of most security incidents can be described as "smart people doing silly things." That's why we must train.
An effective training plan includes four primary characteristics:
- Specific - General topics are not as sticky as specific ones. So instead of email security, discuss phishing.
- Relevant - Each message should be tailored to your specific group. In healthcare, discuss healthcare-specific issues. In financial services, discuss financial services-related topics. In manufacturing … well, you get the idea.
- People-oriented – Center the training not purely on concepts, but take those concepts and put them in the context of what your employees experience.
- Consistent - Whatever your training schedule, stick to it. We find it beneficial to do a quarterly in-person training.
Security is not just a matter of checking a box. We can't just purchase a tool and be in the clear, despite how wonderful that sounds. The ease and mobility of working in the interconnected 21st Century business world comes at a price. That price is security.
Preventative Security Tools
- Technology and Personnel Policies
- External Security Audits
- Security Awareness Training
- Penetration Testing
- Vulnerability Scanning/Assessment
- Risk Assessments
- Security Architecture and Design
Security Assessment
Now is the time to consider the next step toward building a culture of security within your organization. Request a Security Assessment from TekLinks’ team of experts.
Catch up on the rest of the 7 Layers of Data Security series here.
Next week in our final 7 Layer post, we will discuss Monitoring and Response. Learn about about Security Operations.
WHO IS TEKLINKS? A national leader in cloud computing, managed services, engineering services, and value-added resale. We’re a team of expert techies and business professionals who are passionate about building valuable relationships and getting things done right. Simply put: We make IT work for business.