Note: Today is week 9 of a 9-week blog series in which we are peeling back the 7 Layers of Data Security. Catch up on the series here.
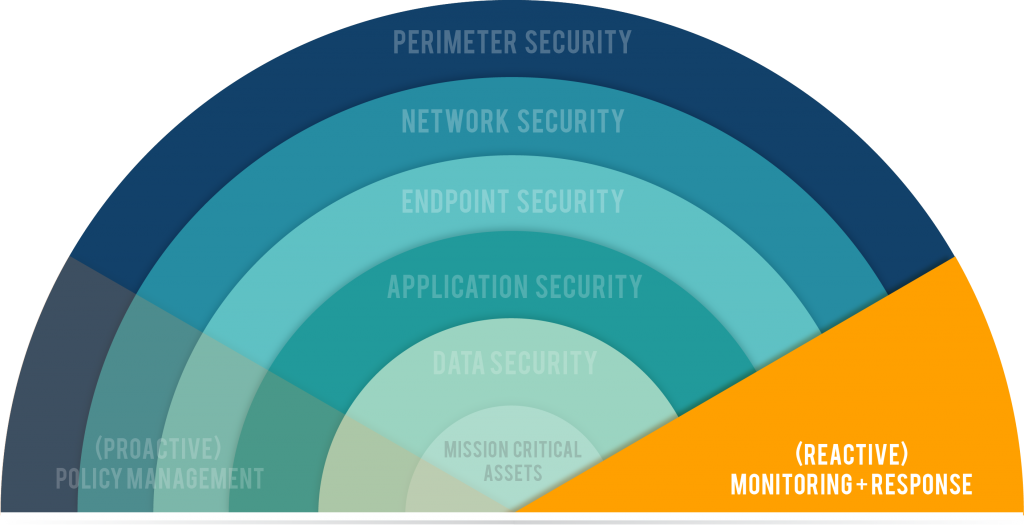
Much of what we’ve discussed already in this series involves setting yourself up for success, laying groundwork. It’s all primarily proactive. The final section involved in securing your technology and data is primarily reactive: Monitoring, and Response/Remediation.
Monitoring
Monitoring is the “neighborhood watch” of your IT environment. Monitoring software works while you sleep. It’s the barking beagle that can’t do much to repel an intruder, but it makes you aware.
Monitoring systems allow you to:
- Identify potential threats within your network
- Observe network hardware performance
- Observe application performance
- Log, analyze, and report on security events
What is a security event?
A security event is a change in the everyday operations of a network, indicating that a security policy may have been violated or a security safeguard may have failed.
Security Information and Event Management (SIEM)
SIEM tools provide the backbone of network monitoring. They live in your network and provide the kinds of data needed in many compliance and regulatory requirements. For instance:
- Data aggregation, which allows you to view information from multiple sources across your network to help avoid missing events.
- Correlation: Looking for common attributes and lumping them together into meaningful bundles of data
- Alerting: Providing notice of issues, usually via a dashboard or email.
- Dashboards: Visualizing your data to assist in identifying patterns or spotting irregular activity.
- Compliance: Generating reports based on the data you need to provide to meet compliance standards.
- Retention: Storing historical data over time to assist in any forensic investigations, compliance, and data correlation.
- Forensic Analysis: Ability to search across logs based on specific criteria.
SOC Monitoring
SOC: Security Operations Center – location where information systems are monitored, assessed, and defended.
Managed Security Services Provider
A Managed Security Services Provider (MSSP) that provides SOC-style monitoring services can filter through many of the issues and alerts generated by your SIEM tool. Then, depending on your setup, will be able to escalate only the issues that are worth investigating or remediating. This drastically reduces the time investment for your staff in observing and fixing possible issues.
MSSPs add value to your security strategy by performing the following functions:
- Monitoring – Listed above.
- Investigation – Research into issues in the logs. Peculiar system behavior. Calling a system in China but we’re not sure why. Investigating this issue might cause hours or days of research.
- Intelligence – What you know about the battlefield and threat landscape helps you interpret what you determine about what’s happening.
- Instant Response – After you do the investigation and determine there’s been a system compromise or security event, it’s responding to that appropriately. That’s where an MSSP can begin the remediation process. This is where a company like TekLinks would tighten restrictions to systems, limit what it can interact with, box it in, and then start cleaning it up, project work to replace that system or decommission it.
IT Paradigm Shift
For leaders to understand the scope of the security discussion, two things need to happen: 1) Leaders must understand that most IT providers and IT personnel are focused on operations. This is a limiting focus and causes big problems. 2) Leaders must understand that they must invest in internal resources or partner with an MSSP in order to do what an operational IT focus cannot. That is, prepare for, audit, analyze, and remediate security issues. The reason traditional staff can’t focus on this is because it’s so outside the scope of what they’re used to, and it isn’t incentivized from the top-down. It’s your job to ensure your company’s security and long-term viability by investing in security.
Remediation and Security Advisory Services
Sometimes, you need someone to just get in and fix your security issues. Perhaps it’s beyond the scope of your staff’s or IT service provider’s skill set. There is an ancient Chinese proverb that applies particularly well in this scenario:
“The best time to plant a tree is 20 years ago. The second best time is now.”
The same goes with security. The best time to get your head around security was 20 years ago. But the second best time is today. Your efforts to understand, anticipate, and prepare your organization for long-term viability through a realistic and achievable security strategy will pay off. Perhaps more than you know.
Consider your peers. After reading this series, you decide to take action to improve your security posture. Over the next year or two, you invest time, resources, personnel into this problem. Your peers may scoff at the extra expense you bring on. But there are two things that they haven’t considered:
- You sleep much better every night than they ever could.
- Left unattended, their technology is a house of cards that will come tumbling down around them.
We applaud your foresight.
Now it’s time to begin the process of improving.
Remember what we said in the first section? Security is a lifestyle, a process of baby steps. And the first step in any security lifestyle journey is to get a risk and vulnerability assessment.
Click here to request a risk and vulnerability assessment from TekLinks.
Read the rest of the series here.
WHO IS TEKLINKS? A national leader in cloud computing, managed services, engineering services, and value-added resale. We’re a team of expert techies and business professionals who are passionate about building valuable relationships and getting things done right. Simply put: We make IT work for business.