 Jordan Helton, a C Spire Azure Solution Engineer, empowers people and businesses to accomplish their goals through the use of intelligent cloud solutions that reduce spend, increase productivity, and harden security.
Jordan Helton, a C Spire Azure Solution Engineer, empowers people and businesses to accomplish their goals through the use of intelligent cloud solutions that reduce spend, increase productivity, and harden security.

There is a lot of FUD (fear, uncertainty, and doubt) associated with utilizing public cloud services. Near the top of that list of concerns is security. Attacks on business networks have never occurred at a higher rate, and that trend has continued to grow over the last several years. For this reason, it is imperative that security be taken seriously no matter where your IT resources are located. The major public clouds like Microsoft Azure and AWS have some of the most secure operating environments on the planet, providing the services and tools necessary to secure your resources. Let's take a closer look at how your security strategy may change as you begin to utilize the public cloud.
Physical Security
Physical security is often overlooked when designing an IT security strategy. Physical security is just as important as any other aspect of protecting your resources. Public cloud providers employ industry-leading standards for maintaining physically secure sites. Because these processes are handled entirely by the public cloud provider, it eases the overall burden of physical security planning and maintenance for the customer. Microsoft recently published a blog on the stringent, layered approach they take to physical security, which you can read here.
Don't forget about those resources located on your premises, with connections into your public cloud infrastructure. They could still be used to compromise your public cloud environment. Therefore, you should continue to adhere to your current physical security strategies and processes for those locations.
User Identity Security
User account compromise continues to be the leading point-of-entry for successful network attacks. Often, it is much simpler to trick a user into giving up sensitive information (such as passwords, or information that can be used to reset a password) than it is to discover and exploit a vulnerable system. For this reason, securing user identities should be a top priority in your organization. Here are some suggestions on how you may strategize in this area:
- You have likely already, or are considering, extending your user identities to Azure Active Directory (Azure AD is the authentication system for Office 365). Layer additional security protocols on top of the previously mentioned modern authentication. This could include Multi-Factor/Two-Factor authentication and user behavior monitoring solutions (such as Azure Advanced Threat Protection).
- Configure SaaS applications to utilize Azure Active Directory where possible. This will minimize the amount of accounts each user must keep up with and allow for better administrative control. At the time of this writing, there are nearly 3000 applications in the Azure AD Application Catalog, and custom applications can also be configured.
 Azure Active Directory Application Catalog
Azure Active Directory Application Catalog
- Protect users at their most vulnerable points (e-mail) by incorporating additional tools such as Office 365 Advanced Threat Protection, to guard against attacks such as Spoofing, Spear Phishing and malicious files.
- Update your User Awareness Training to reflect modern systems and types of attacks.
- Consider modern tools to track points of access into the network, such as VPN logons. For example, tracking user VPN logons using Azure Operations Management Suite.
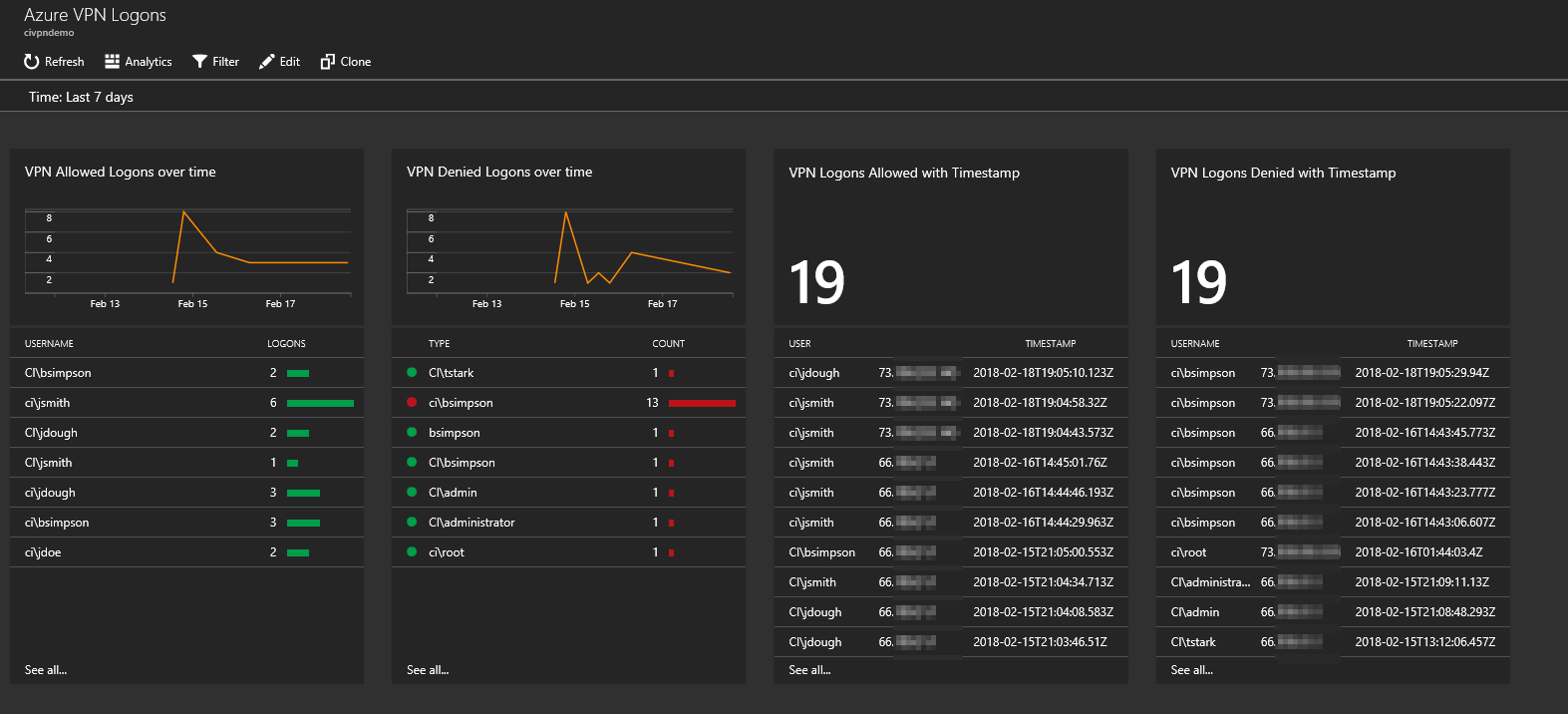 Example Azure OMS Dashboard for tracking VPN logons
Example Azure OMS Dashboard for tracking VPN logons
Data Security
Perhaps the biggest concern we hear about when migrating to public cloud is data security. Businesses are apprehensive to trust their data residing in a third-party datacenter and wonder exactly who can access that data. The good news is that all the major public cloud providers go into extreme detail as to policies and procedures that govern where your data is stored and accessed. Ensure you have reviewed your selected providers documentation to fully understand these details.
Many of the same approaches used to secure on-premises data will remain the same in public cloud, especially If you are utilizing Infrastructure-as-a-Service (IaaS). Ensure that your data is encrypted at rest (VM disk encryption, Storage Account Encryption) and in-transit (TLS Certificates, IPSEC VPNs, or other encrypted protocols). For increased levels of security, you may even consider offerings such as Azure Private Instances, where the entire physical server hosting your virtual servers is only occupied by your resources.
As you modify your approach to security when migrating to public cloud, consider new and emerging tools that were born in the cloud. Azure Security Center and Azure Operations Management Suite offer next-generation capabilities to transform how you approach security in your current systems. These tools not only monitor public cloud resources, they can also be used in a hybrid scenario with your on-premises resources.
Perhaps the largest delta of change in your security strategy will be realized as you start to utilize Platform-as-a-Service (PaaS) offerings in public cloud. These are services where the underlying virtual machines are abstracted away from you and managed by the provider, allowing you to focus on the workload itself, rather than the resources powering it. Where there is huge pay-off in terms of no longer managing patching or updates, there exists greater risk if you are unfamiliar with how these resources are secured and tie into your existing resources. Ensure that you are intimately familiar with your public cloud provider's platform and how they secure PaaS offerings, or work with a partner with expertise in this area.
Network Security
In most security strategies, more time is probably spent on network perimeter security than any other aspect. This is because of the assumption that if an attacker can’t get into an environment, they can’t do much damage. Although this isn’t entirely true, a robust external and internal network security strategy is key to the integrity if any IT infrastructure.
As discussed previously, many of your existing strategies will stay the same when securing network resources in public cloud. Ensure that allcommunications to your public cloud infrastructure are encrypted, and open ports into your network only when necessary. The major public cloud platforms provide native network security tools to assist in securing your resources. For example, in Microsoft Azure a native resource called a Network Security Group is used to provide firewall capabilities for virtual network subnets or virtual servers. Azure VPN Gateways can provide encrypted connectivity to your on-premises networks, and Azure Application Gateways can be used to front-end web facing applications hosted in Azure. Additionally, Web Application Firewall services can be added to the Application Gateway to protect against common internet attacks.
If you find that native tools and services are not comprehensive enough for your needs, you can also choose to run full next-generation firewalls from major networking vendors (including Cisco, Fortinet, Palo Alto) in your public cloud environments. Other network security appliances are also available, such as Citrix NetScaler.
An important aspect of network security is knowing when an incident occurs, or a configuration has changed. For example, it doesn’t matter if we close a network port if that port is opened again a day or two later. Consider integrating tools such as Azure Security Center and Azure Policy into your strategy. Azure Security Center will notify you if a port is opened to a resource within your public cloud environment, make suggestions on security layers to add to your infrastructure, and even monitor your resource for attacks and breaches. Azure Policy can be used to enforce rules upon your public cloud infrastructure, ensuring that staff managing the environment can’t make changes detrimental to security. For instance, Azure Policy can be configured to outright block the addition of public IP addresses, or the opening of ports to the internet. If you plan on employing a hybrid cloud strategy, consider utilizing a toolset that can manage and monitor all your resources no matter where they exist. A great example is C Spire Threat Management. This Security-as-a-Service offering combines a network security monitoring tool (which can monitor your switches, firewalls, WAPs, storage, compute, users, operating systems and more across any premises, public cloud or datacenter) with an SLA-backed live technician review and response service.
Identify, Strategize, Secure
As you can see, securing resources in public cloud boils down to a hybrid strategy. Combining best practice methodologies, traditional infrastructure, and modern cloud tools and offerings will provide you with a layered security approach for your journey to the cloud. If you need assistance in this area, contact TekLinks experts here. Our team provides these services and employs experts in public cloud and security to augment your staff and help your business achieve its goals.
Contact C Spire here.

















