 Do you allow your employees to check their personal email while at work? Are they permitted to use their work email addresses for shipping notifications from online retailers?
Do you allow your employees to check their personal email while at work? Are they permitted to use their work email addresses for shipping notifications from online retailers?
If you answered “yes” to these questions (as most businesses do), you may have increased risk and exposure during the holiday season. Professionally as an Ethical Hacker, I am paid to socially engineer my way into other company’s networks using phishing emails exactly like the one that my wife received earlier this month:
At the end of November, our three boys were excitedly looking forward to a Lego Star Wars holiday advent calendar arriving from Amazon.The basic idea is that there is something new to build every day leading up to Christmas. It was expected to arrive sometime before Dec. 1.
However, on Dec. 1, it still hadn’t arrived – despite showing as delivered within our Amazon account. Then my wife received the following message:
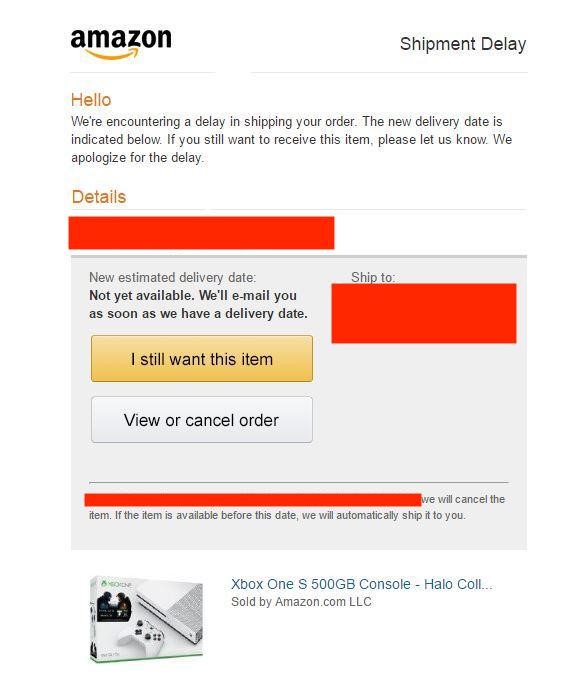
I’d like to tell you that we quickly and easily determined that the above message was a phishing email, designed to trick us into logging into a fake website that would collect our Amazon login credentials. However, we almost missed it! While not intentional on the sender’s side, the timing of message was perfect. We were also frustrated and looking for answers regarding the delay, too. Thankfully, we ultimately didn’t fall victim to the phishing attempt and Amazon was able to get the issue resolved for us. On Dec. 3, instead of building only one item, each of our three boys built a Lego so we could catch up on the calendar for the next day. In the end, everything worked out great and everyone was happy with the outcome – especially our boys.
5 Steps to Protect Yourself
This is holiday season, it is very likely that cyber criminals will target your business by engaging with your employees under the auspices of an important message from an online retailer. Often, clicking on the links within these messages will attempt to download malicious software that will give the attacker remote access to the corporate network via a compromised computer. They may also try to coerce employees into providing their personal passwords to legitimate sites – like Amazon. However, their ulterior motive may be to find instances where people are sharing their corporate password with a personal account.
 Despite repeated warnings, we find that many employees share passwords across personal and work platforms. This can put your company at great risk – especially if an employee falls for a personal phishing attack and is reusing that password on one of your corporate systems (like a VPN). Unfortunately, cybercrime is an extremely lucrative and multifaceted business. Collectively, victims of cybercrime lost approximately $172 billion dollars in 2017 (globally).
Despite repeated warnings, we find that many employees share passwords across personal and work platforms. This can put your company at great risk – especially if an employee falls for a personal phishing attack and is reusing that password on one of your corporate systems (like a VPN). Unfortunately, cybercrime is an extremely lucrative and multifaceted business. Collectively, victims of cybercrime lost approximately $172 billion dollars in 2017 (globally).
With the holiday season in full swing, it’s more important than ever to encourage employees to be vigilant and on the lookout for holiday phishing scams. Not only personally – but also understanding the potential impact of clicking on a link within their personal email at work. In my opinion, this is an attack vector that many companies don’t typically consider.
Below are 5 steps everyone can take to better protect themselves (and the company) this holiday season:
- Be especially wary of order and delivery confirmations. Instead of clicking on the links within these emails, go to the website manually to get the update.
- Don’t reuse passwords. Anywhere. Ever. If one website (or password) is compromised for some reason, you don’t want to be a position of having everything compromised.
- Turn on multifactor authentication wherever possible. Even if a criminal is able to get your password, you can protect yourself by requiring an additional form of authentication to your account.
- Use a credit card instead of a debit card when shopping online. It is easier to deal with fraudulent purchases when you use a credit card.
- Monitor bank accounts and your credit cards at least three times a week. If you are shopping online, you should be checking your accounts at the end of each day. You can also set up text alerts for any purchases for $1 – to ensure you’re aware of every purchase being made.
Nick VanGilder is an Ethical Hacker and co-leader of C Spire's Cybersecurity Consulting Group.














![[Up Next: 8 Tips to Stop Password Hackers]](https://no-cache.hubspot.com/cta/default/464523/1974e1d8-c383-4adf-a203-ca85b50b3482.png)



